Join Our Telegram channel to receive the latest updates on breaking news stories
The Lazarus Group, an infamous hacking collective believed to be backed by the North Korean government, has reemerged after months of inactivity. In their latest operation, this group leveraged a counterfeit non-fungible token game on Google’s Chrome browser, deploying spyware that compromised crypto and NFT wallet credentials.
Lazarus Crypto Hacker Group Makes a Comeback
On October 24, Cointelegraph.com, a leading crypto news outlet, reported the resurfacing of the Lazarus hacker group after a quiet period. The group initiated their comeback with the rollout of a phony non-fungible token game on Chrome, which included spyware that gathered sensitive data from gamers interacting with it.
The #NorthKorean #Lazarus hacking group took advantage of a Google Chrome zero-day vulnerability, tracked as CVE-2024-4947, via a fraudulent decentralized finance (DeFi) game aimed at crypto users. #Hacking #cybersecurity https://t.co/wMBJUipAq4
— Anonymous
(@YourAnonRiots) October 23, 2024
The Lazarus Group is recognized as a state-sponsored cyber threat organization linked to the North Korean Reconnaissance General Bureau (RGB). This intelligence agency was formed to conduct surveillance, execute covert missions, and engage in cyber operations. Since its establishment, the RGB has focused extensively on gathering intelligence and infiltrating cryptocurrency assets from South Korea, the United States, and Japan.
The group gained notoriety in 2021 after a major breach at Sky Mavis, the company behind the well-known blockchain game Axie Infinity, led to a loss of hundreds of millions in assets. Following an extensive probe, the FBI officially tied the breach to the Lazarus Group. North Korean hackers have a documented history of cryptocurrency heists, accumulating over $3 billion by December 2023.
Lazarus Hacker Group Strikes Again in 2024
According to the Cointelegraph analysis, Kaspersky Labs first detected the exploit in May and notified Google, which resolved the issue shortly after. The hackers promoted a play-to-earn multiplayer game on LinkedIn and X, deceiving users with non-fungible tokens serving as tanks in a global competition. Microsoft Security Team identified and flagged the fraudulent NFT game in February 2024.
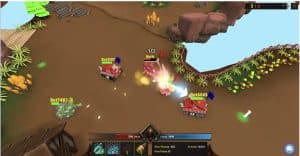
Image from Lazarus Group’s counterfeit game. Source: SecureList
The North Korean hackers had eliminated the exploit from the site before Kaspersky could assess it. Nevertheless, Kaspersky Labs informed Google, which patched the flaw in Chrome before the hackers could exploit it again. Currently, the total number of victims affected by this breach remains uncertain. Users who interacted with the game are encouraged to reset their passwords.
Related NFT News:
Most Searched Crypto Launch – Pepe Unchained
- Layer 2 Meme Coin Ecosystem
- Featured in Cointelegraph
- SolidProof & Coinsult Audited
- Staking Rewards – pepeunchained.com
- $10+ Million Raised at ICO – Ends Soon
Join Our Telegram channel to receive the latest updates on breaking news stories









