This article is part of Bitcoin Magazine’s “The Privacy Issue”. Subscribe to get your copy.
Privacy represents a critical concern when utilizing a public blockchain like Bitcoin. Over the years, various projects and proposals have emerged, aiming either to create privacy-preserving tools that operate on top of Bitcoin or to fundamentally enhance privacy at the protocol level. Even Satoshi briefly considered zero-knowledge proofs as a means to bolster user privacy before his departure.
The original whitepaper contained the following remarks regarding privacy:
10. Privacy
The conventional banking system offers a degree of privacy by restricting access to information to the involved parties and a trusted third party. However, the necessity for public transaction announcements prevents this approach. Nonetheless, privacy can be preserved elsewhere by ensuring public keys remain anonymous. The public can observe that a certain amount is being sent to another party without having any information linking the transaction to specific individuals. This resembles the disclosure level seen in stock exchanges, where transaction times and sizes are publicly available, but the identities of the trading parties are kept confidential.
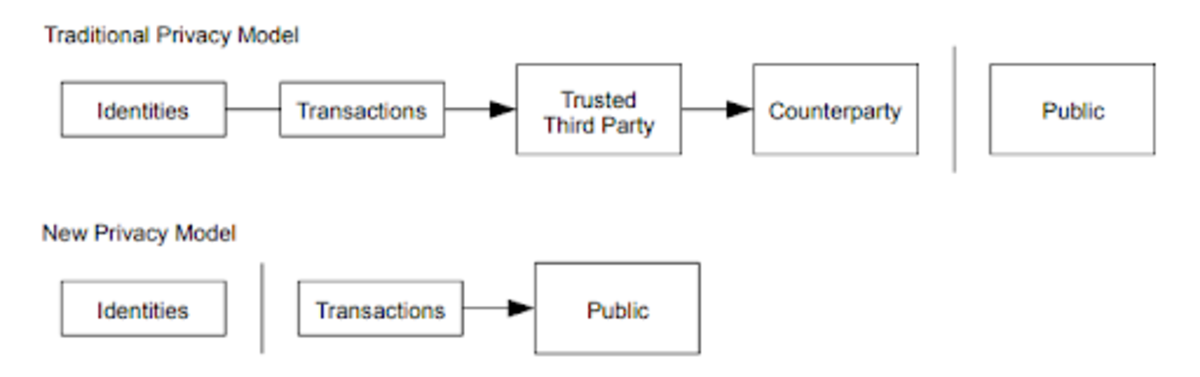
To enhance privacy, a new key pair should be generated for each transaction to prevent links to a common owner. Some degree of linking is inevitable with multi-input transactions, which reveal that all inputs were controlled by a single owner. The risk lies in the potential exposure of a key owner, which could lead to the disclosure of other transactions linked to them.
——————-
That’s it. This was the extent of Satoshi’s guidance regarding the transactional privacy of Bitcoin users. His advice entailed not reusing addresses and carefully considering the combined expenditure of coins, as doing so creates transparent ownership connections on the blockchain. Fifteen years later, we have amassed enough knowledge and experience to recognize that this section of the whitepaper is quite lacking.
It merely served as a conceptual framework within which the private or non-private use of Bitcoin could develop over the following decade. Advising users to refrain from combining coin expenditures is as practical as suggesting a person should only spend a single cash note forever. It was inevitable that as Bitcoin was used as a currency, individuals would frequently need to spend multiple coins together, thereby linking their funds over time through successive transactions.
Basic heuristics such as combined coin expenditures are fundamental to blockchain analysis and the tracing of individuals’ transaction histories. If multiple coins are spent in one transaction, it can be reasonably inferred that they belong to the same individual. If an address receives coins from various sources, it indicates ownership by one person. As large quantities of coins are spent together and connected over time, they form clusters. These basic heuristics are what render Bitcoin’s blockchain non-private, as transactions can be observed on-chain and these rules applied.
Now, before we delve deeper, it’s vital to emphasize that while this point is crucial for understanding, it doesn’t provide any reasonable or useful proactive privacy measures for users. This reflects a fundamental flaw in Bitcoin’s design: the protocol lacks tools or architecture to inherently safeguard user privacy, leaving this responsibility entirely to the users.
Choosing Privacy
Throughout the years, several protocols have been designed to remedy this issue:
- Coinjoins: Protocols where users collaborate to consolidate their coin expenditures, enabling them to send equal amounts to different addresses within the same transaction, thus obscuring which coins belong to whom.
- Coinswap: Protocols allowing users to privately exchange coins through two transactions, with no visible link on the blockchain as long as both parties cooperate.
- Chaumian Ecash Mints: Protocols allowing a centralized entity to issue cryptographically blinded tokens. This structure ensures that the issuer can’t identify which token corresponds to a user when they go to redeem that token, enabling highly private transactions.
- Confidential Transactions: An essential component of Monero, originally developed by a Bitcoin developer. These obscure the transaction amounts through cryptographic blinding while providing a proof that outputs equal or are less than inputs, without revealing specific amounts. While inefficient at the time proposed, it could exacerbate Bitcoin’s scaling issues and allow a quantum attacker to inflate the Bitcoin supply undetected or reveal the entire transaction history if they break the cryptographic assumptions of Bitcoin.
- Zerocoin: A proposal aimed at facilitating deposit into a single “escrow pool” and allowing later withdrawals without an easily traceable on-chain history, verified through a zero-knowledge proof. It never saw implementation due to being computationally demanding at the time.
The first two proposals operate at the application layer, easily buildable on Bitcoin without requiring changes. The latter two necessitate fundamental upgrades at the protocol level, which cannot be executed immediately without achieving consensus on the trade-offs involved. I personally believe that such upgrades are unlikely to occur.
This leaves us with actionable paths forward. Numerous tools have already been developed, with many more yet to come, but our progress in enhancing privacy relies on tools that individuals must choose to use. If nobody utilizes these tools, they become ineffective. In a public landscape like Bitcoin, privacy cannot be achieved in isolation; collaboration is necessary to cultivate an environment where privacy can thrive. This is a personal choice but has significant consequences for the broader Bitcoin community.
It stands as one of the most consequential decisions regarding Bitcoin.
Should individuals fail to prioritize their privacy and take measures to uphold it, Bitcoin’s privacy will diminish. It risks becoming forbidden, initially marginalized before later facing active restrictions and penalties. Governments will stigmatize it, impose regulations, and restrict it to a small, obscure segment of society. At that point, Bitcoin’s privacy will have effectively failed.
Even Eric Hughes, author of the Cypherpunk Manifesto and creator of the phrase “cypherpunks write code,” later recognized that code alone doesn’t suffice:
“Perhaps the single most important lesson I’ve learned from cypherpunks is that code alone doesn’t cut it. Not code alone, not code widely distributed, not even code widely used. Some measure of toleration in society for activities conducted in private is necessary for long-term success. Not convenient, not easier, but necessary.” -Eric Hughes, Cypherpunk Mailing List Mar 14, 1996.
Individuals must choose to value privacy collectively. It needs to be widely regarded as important—important enough that people will act despite coercion or intimidation to protect it. Society must widely accept privacy, akin to how free speech is valued in America or the right to bear arms. It should be so broadly supported that even in the face of strong opposition from certain groups, governments will refrain from outright suppression due to the extensive backing.
People must defy such attempts in sufficiently large numbers that enforcement becomes socially and practically unfeasible. This decision and subsequent actions are inherently political, a political act.
Action is imperative; otherwise, this battle may already be lost.
Building Privacy
Assuming people will take action in sufficient numbers to be impactful, what exactly should they do? Without fundamental protocol changes, individuals must select specific tools to maintain their privacy. Which tools? How do they function?
We mentioned a few tools earlier, but a more in-depth and holistic perspective on their functions is necessary. Understanding how these tools can work in tandem is essential. Viewed in isolation, it may seem that any particular privacy tool on Bitcoin is insufficient technologically. Yet, when considering their combined usage, it’s clear that a substantial level of privacy can be attained if users adopt them collectively.
Most Bitcoin functionalities are composable; no tools exist in isolation. Various applications can synergize, whether through integration into single tools or through the joint use of multiple tools. Let’s review the current landscape from upper layers down to the base layer.
Chaumian Ecash
Chaumian ecash mints represent an established concept that predates Bitcoin by decades. David Chaum conceived of it in 1982. Chaumian ecash utilizes blind signatures to create a private payment system. In this model, a central mint server acts as a token issuer, managing the creation of new tokens backed by deposits and redeeming tokens to facilitate transactions. The privacy of these transactions is enabled by the blind signature mechanism.
Each token is essentially a random value endorsed by the mint. In a basic iteration of this scheme, the mint can track the redemption of each token it signs and correlate the redeemed and issued tokens, thus accessing their transaction history. By blinding each token value before submission to the mint for signing, the mint remains unaware of the specific value it endorsed. After receiving the mint’s signature, users can unblind it, resulting in a valid signature for the plaintext value they generated.
The mint would only encounter a plaintext token when it is redeemed for a new one, and since the token was blinded during the signing process, it remains ignorant regarding the timing or identity of the signer. This allows for centralized yet highly private transactions, enabling users to achieve a near-perfect level of privacy at the cost of trusting the operator with their funds. There are no liquidity issues or other shortcomings associated with protocols like Lightning, allowing any user willing to trust a mint to receive money privately through token exchange.
Furthermore, ecash offers possibilities beyond mere private scalable payments; the tokens can also be made programmable. When utilizing a Chaumian mint, users trust the operator to handle payments honestly and not misappropriate their funds. There’s no reason these operators can’t extend beyond processing payments to enforcing smart contracts.
Just as Bitcoin script enables programming conditions for spending bitcoin, mints could employ scripting or other programming languages to incorporate conditional spending requirements into ecash tokens. Instead of generating a random value for the mint to sign, users could produce a script program to blind. Upon signing, the mint retains visibility over the script when redeeming the token but can only authorize redemption if the script requirements are fulfilled.
Various trust models are possible, with more likely emerging as innovative thinking continues. The simplest model involves a single operator like any custodial system, such as Coinbase. Alternatively, a federated operator spreads trust among multiple parties, placing ecash on par with other systems considered decentralized. Some models even propose inverting the risk, with the Chaumian mint issuing tokens backed by its funds, lending to users, and periodically collecting debts.
As we can see, considerable privacy can be achieved at this juncture…but at the potential cost of diminished sovereignty and control over our funds. Though far from ideal, this remains an accessible option today, contingent upon sufficient numbers of users operating these systems and solutions allowing interaction across various mints.
Enter the Lightning Network. It provides seamless deposits and withdrawals for users engaging with a mint, facilitating quick settlement processes for users cashing in a mint from one token and transferring it to another mint of their preference.
Lightning Network
Lightning operates as a network of bi-directional payment channels, enabling users to route payments off-chain across its structure. Users collaborate to lock funds within a two-party multisig address, deploying pre-signed transactions to ensure that each party can retrieve their funds independently if necessary. Once established, the funds’ balance can be updated off-chain through signing a new series of transactions and exchanging penalty keys, allowing the other party to confiscate all funds for any cheating attempts using outdated transactions.
While Lightning is not without flaws, it significantly improves privacy compared to on-chain Bitcoin usage by simply not recording every transaction onto the blockchain. Instead of permanently tracking each transaction’s origin and destination, the only visible entry on the blockchain is the creation of the payment channel itself. The specifics of payments made or received remain hidden from the general public, with only the identity of the party with whom the channel was established visible.
Concerning off-chain footprints, things are somewhat nuanced. Receivers currently expose their Lightning node to anyone sending them payments. This could potentially be resolved by BOLT 12, a proposal introducing a scheme known as blinded paths that obfuscate the receiver’s Lightning node from the sender by having them compute the last hops in their payment route. Senders, on the other hand, enjoy excellent privacy as recipients cannot ascertain their Lightning node or funds.
Yet, Lightning poses unique challenges for end users. Specifically, there’s the prerequisite to allocate liquidity with channel counterparts to receive funds, leaving recipients unable to accept more money than their counterparties can route. As a payment routing network, it performs admirably if users can address liquidity issues.
Most users tackle these challenges by engaging a Lightning Service Provider (LSP), which fulfills the role of providing liquidity for receiving payments. However, this comes with privacy trade-offs, as the LSP, by serving many users, learns about numerous users’ payment activities. In some cases—particularly when LSPs employ Trampoline Routing (a method where the LSP calculates payment routes for users)—they may even ascertain the destination of their users’ payments.
Many of these challenges can be mitigated by integrating Chaumian ecash mints with Lightning. By having multiple users utilize a single Lightning node operated by the mint, liquidity can be efficiently pooled, allowing all users to receive funds without individual limitations. The anonymity provided by ecash can also shield users from some privacy shortcomings associated with Lightning. Even when the mint, as the Lightning node operator, knows where payments are routed across the network, it remains oblivious as to which user(s) made those payments.
Although utilizing Lightning directly by a user offers less privacy than Chaumian ecash—and does come with the added challenges of sourcing receiving liquidity and interacting with LSPs—it does not necessitate giving up control of one’s funds. While it may not scale as effectively as ecash and is more complex to navigate, it supports a superior trust model.
It is crucial to note, however, that Lightning does not completely obscure the ability to trace coins on-chain. While it may hide the specific details of individual off-chain transactions, coins entering a channel and their movements upon closure remain traceable.
Coinjoins
Coinjoins are a protocol enabling multiple users to work together in crafting a transaction that complicates or nullifies the tracking of their coins. Heuristics such as common input ownership and clustering primarily underpin the tracking of funds. Disrupting these heuristics is the key to ensuring privacy. Coinjoins accomplish this by distinctly structuring the inputs and outputs of a transaction.
For example, if five people aim to obscure their transaction history, they can combine their coins into a single transaction while all generating outputs of equal amount. This creates a false indication of shared ownership and a deceptive cluster since the outputs, being equal, cannot reliably disclose which coins belong to whom when transacted in the future.
Now envision a Lightning user. Even if they maximize their privacy via Lightning, they must still consider the implications of their blockchain interactions. If a user withdraws coins from a KYC-compliant exchange and establishes a Lightning channel, they could conduct numerous transactions off-chain. However, if they close that channel with fewer funds than what they initially deposited, the exchange will at least confirm that they spent that amount somewhere.
When they subsequently use these coins alongside known coins or open a new Lightning channel linked to their node, the exchange can ascertain a stronger confidence that they are still controlling those funds. These connections necessitate obfuscation, which is where Coinjoins come into play.
Coinjoin emerged as the most widely implemented base layer privacy solution, with the two leading examples being Wasabi by ZKSnacks and Whirlpool by Samourai. Samourai ceased operations following the arrest of its founders, while Wasabi voluntarily discontinued its coordinator shortly after. Both systems relied on a centralized coordinator server to facilitate coinjoin transactions for users.
Joinmarket, another operational option, utilizes a decentralized model where “takers” (users) select from a market of “makers” (liquidity providers) to arrange coinjoins. However, Joinmarket lacks the development and support of a company backing, existing solely as an open-source project.
These are not the only available alternatives. Users can re-establish a Wasabi or Whirlpool server if desired and even engineer novel coordination models for serverless coinjoins. The coordination of a coinjoin transaction and its execution are related yet distinct components. There are myriad approaches to achieving the goal of coordinating coinjoin creation, and importantly, it remains permissionless to experiment with new methodologies.
The Holistic Stack
Now that we’ve examined these components, consider their interrelations and how they collaboratively maximize privacy across layers. Users engaging with an ecash mint experience substantial privacy, even from the mint operators themselves. Those mint operators can leverage Lightning to attain significant privacy for both themselves and their users interacting with various mints, while coordinated liquidity strategies can keep public blockchain activities obscured.
Even without radical changes to Bitcoin, there exists a viable path from our current state towards a private and censorship-resistant Bitcoin. While it may not be ideal and can involve costs and complexities or require compromises on trustless goals, it is attainable.
As we progress, improvements to the Bitcoin protocol will enhance these capabilities further. Covenant schemes strengthening scalability could alleviate challenges present in systems like Lightning, enabling more users to engage privately while self-custodying their funds instead of relying on Chaumian mints.
Some scaling enhancements may even reduce the necessity for on-chain privacy solutions like Coinjoins, as more individuals share custody of one coin in a trustless environment, producing natural ambiguity regarding user actions when withdrawals are made.
A viable path forward exists now, and its prospects will brighten with each enhancement to the Bitcoin protocol. Ultimately, it requires users to choose to walk this path.
A Future With Privacy, Or A Future Without
For some, privacy may seem trivial or unimportant. “What do you have to hide?” Such individuals often fail to recognize the serious implications of living without privacy. Observing current societal dynamics, it is clear how quickly individuals can be ostracized or shamed for minor infractions—holding an unpopular opinion, articulating a controversial thought, or backing the “wrong” political figure.
Increasingly, the absence of privacy threatens severe and traumatic consequences for individuals. It is crucial that people retain control over what information about themselves gets publicly disclosed. This issue transcends mere criminal concealment; it’s about allowing everyday individuals to shield themselves from societal pressures and repercussions.
For those living under tyrannical or oppressive governments worldwide, the stakes of maintaining privacy extend beyond job loss or social standing; they can literally risk their lives.
Privacy can be the difference between safety and peril, even in ostensibly secure and free jurisdictions. Imagine transacting with someone while inadvertently disclosing your substantial bitcoin holdings; you may unwittingly expose yourself to physical danger. Numerous cases illustrate kidnappings, assaults, and even torture inflicted by criminals seeking to seize bitcoin from those revealing wealth.
Even scenarios involving domestic violence underscore the crucial need for privacy. Many individuals remain in abusive relationships because of financial dependency. How can a person in such a situation strive for economic independence without privacy? Without being able to save and earn discretely, without a partner discovering their efforts?
Privacy is paramount.
Returning to Bitcoin, one of its core attributes is its censorship resistance—the ability to transact freely and independently, without seeking permission from anyone or facing disruptions.
However, transactions involve two parties: a sender and a receiver, a buyer and a seller. If governments, regulators, or the public can trace your payments and bitcoins in public channels, how can genuine censorship resistance exist? How can it function if any authority or collective can intimidate or coerce people into eschewing transactions with you? If a merchant must fear that accepting “tainted coins” may lead to governmental scrutiny and financial loss due to confiscation, then true freedom dissipates.
When coins can be meaningfully distinguished and followed through their movements, Bitcoin risks disintegrating into an ineffective form of currency. For money to operate effectively, it must be fungible—i.e., all coins must remain indistinguishable from a merchant’s perspective. To achieve fungibility, privacy is essential.
Privacy, fungibility, and censorship resistance are intertwined aspects of a single ecosystem—they can only coexist together.
Individuals must choose to uphold privacy; otherwise, Bitcoin risks losing its censorship resistance. Many may not adopt privacy as a priority on ideological or political grounds but need to actually witness its utility. They must experience the practicality of donating to causes important to them without fear of backlash. They need to recognize how it helps activists in oppressive states achieve meaningful outcomes. They need to see how online privacy can disrupt intrusive targeted advertising.
This is perhaps the most significant battle Bitcoin faces, and we currently stand at a critical turning point in that struggle. The outcome of this battle will determine Bitcoin’s future. Will it serve as a vessel for sovereignty and freedom, or will it morph into a mechanism for surveillance and oppression? The answer lies in our collective choices.
I refuse to live in a world devoid of privacy—of thought, interaction, or transaction—where each action, every utterance or private thought, lies under the scrutinizing gaze of the government and societal mobs. Where slight missteps can obliterate lives, leaving no space for dissent, dialogue, or debate.
I choose privacy. I choose censorship resistance. I choose freedom.








